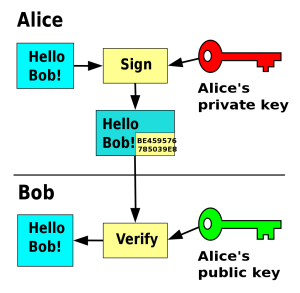
Some time you need to create self-signed certificates for public / private keys.
The software can help you do that is “OpenSSL”.
I will declare detail steps.
1. What do we need?
we do need server public / private key & client public / private key.
2. How do we do?
I will demo the step on Ubuntu desktop which installed openssl.
First, we need to create the C.A certificate
Create CA key
$ openssl genrsa 2048 > ca-key.pem
Output:
Generating RSA private key, 2048 bit long modulus (2 primes)
...............................................+++++
....................................+++++
Generate CA cert
$ openssl req -new -x509 -nodes -days 3650 -key ca-key.pem -out ca-cert.pem
<console/output>
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:VN
State or Province Name (full name) [Some-State]:Ho Chi Minh
Locality Name (eg, city) []:Ho Chi Minh
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Your company
Organizational Unit Name (eg, section) []:.
Common Name (e.g. server FQDN or YOUR name) []:Your company
Email Address []:.
Then, I will create public / private keys for the server which are signed by C.A Cert above.
Create Server Private Key & Cert Request
$ openssl req -newkey rsa:2048 -nodes -days 3650 -keyout server-key.pem -out server-req.pem
<console/output>
Ignoring -days; not generating a certificate
Generating a RSA private key
....................................................................+++++
.................+++++
writing new private key to 'server-key.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:VN
State or Province Name (full name) [Some-State]:Ho Chi Minh
Locality Name (eg, city) []:Ho Chi Minh
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Your company
Organizational Unit Name (eg, section) []:.
Common Name (e.g. server FQDN or YOUR name) []:My Server
Email Address []:.
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:.
An optional company name []:.
Generate Server Cert
$ openssl x509 -req -days 3650 -set_serial 01 -in server-req.pem -out server-cert.pem -CA ca-cert.pem -CAkey ca-key.pem
<console/output>
Signature ok
subject=C = VN, ST = Ho Chi Minh, L = Ho Chi Minh, O = Your Company, CN = My Server
Getting CA Private Key
Now, we can verify the Server Cert by C.A Cert, if this step ok, you might do it right.
$ openssl verify -CAfile ca-cert.pem ca-cert.pem server-cert.pem
<console/output>
ca-cert.pem: OK
server-cert.pem: OK
Same as the Server, we could create client public / private keys
Create Client Private Key & Cert Request
$ openssl req -newkey rsa:2048 -nodes -days 3650 -keyout client1-key.pem -out client1-req.pem
<console/output>
Ignoring -days; not generating a certificate
Generating a RSA private key
....................................................................+++++
.................+++++
writing new private key to 'client1-key.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:VN
State or Province Name (full name) [Some-State]:Ho Chi Minh
Locality Name (eg, city) []:Ho Chi Minh
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Your Company
Organizational Unit Name (eg, section) []:.
Common Name (e.g. server FQDN or YOUR name) []:Client 1
Email Address []:.
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:.
An optional company name []:.
Client Cert
$ openssl x509 -req -days 3650 -set_serial 01 -in client1-req.pem -out client1-cert.pem -CA ca-cert.pem -CAkey ca-key.pem
<console/output>
Signature ok
subject=C = VN, ST = Ho Chi Minh, L = Ho Chi Minh, O = Your Company, CN = Client 1
Getting CA Private Key
Verify client cert:
$ openssl verify -CAfile ca-cert.pem ca-cert.pem client1-cert.pem
<console/output>
ca-cert.pem: OK
client1-cert.pem: OK
Important notices:
- Make sure every server/client key set has its own Common Name (C.N). If a key does not have C.N, the handshake verify will be failed.
- Make sure you sign your key sets by the C.A cert and delivery the C.A cert come with the public (cert) / private keys of server or clients.